Phishing emails are malicious messages that attempt to trick recipients into providing sensitive information or performing fraudulent tasks. Users can report any suspicious or malicious message to LSU IT Security and Policy (ITSP) for review through the Report options in Outlook.
Remember, LSU will never:
- Ask you for your password over email, phone, text, or through a form submission for your LSU account or any other account
- Ask you to approve a log in through a phone call or your Microsoft Authenticator app for a sign on you are not attempting
- Initiate unsolicited phone calls or text messages requesting sensitive personal information such as your full name, date of birth, LSU ID number, or Social Security number
- Ask for payment through PayPal or Zelle to retain your account
- If you believe you may have fallen for a phishing email, review the guidance below
Phishing Examples
This article describes and provides examples for the following malicious message types:
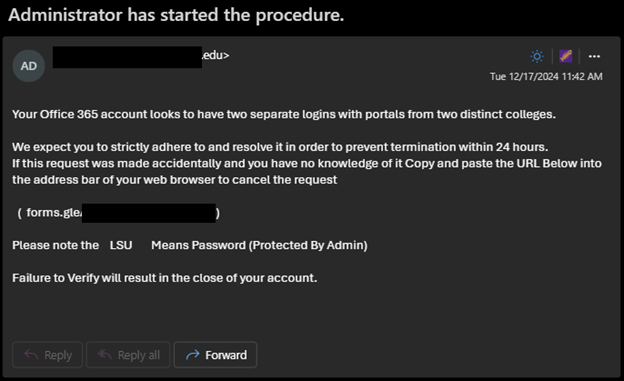
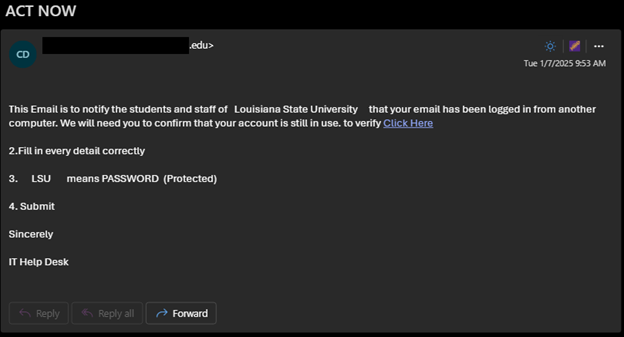
Victims receive the threat that there are various issues with their account that require attention before the account is deactivated.
These phishing attempts encourage users to visit phishing sites or forms that request personal contact information and account passwords.
Attackers may attempt to collect phone numbers or personal email addresses to continue the scam outside of the LSU.EDU environment, such as over text message, where messages cannot be blocked or monitored by LSU security controls.
Never provide your password to third parties!
[back to top]
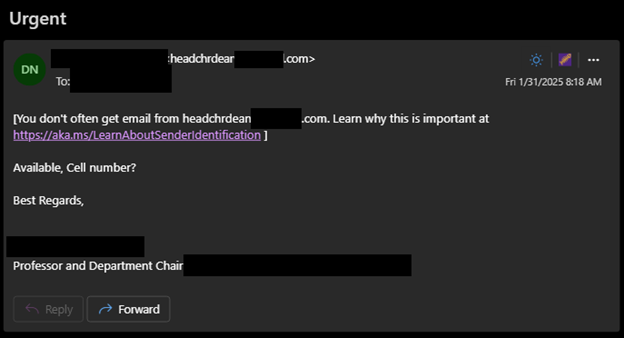
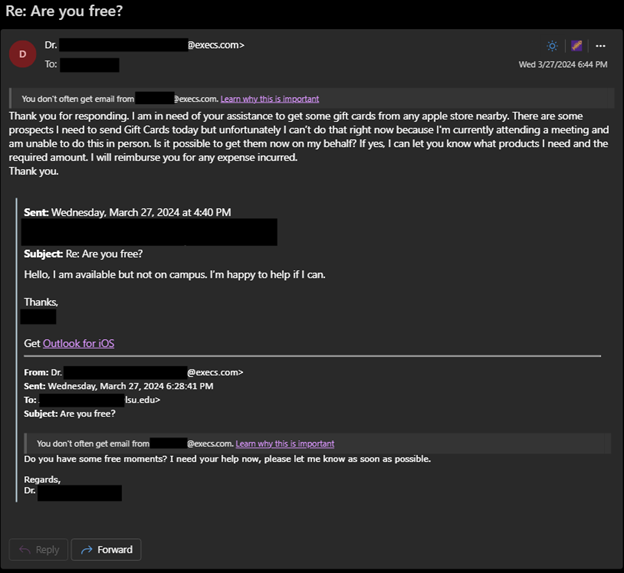
Attackers take information from publicly available listings like staff directories or membership lists from groups or organizations to impersonate someone to their peers and other contacts by creating new accounts with free email providers that use an individual's name, department, or title in the email address or their display name.
The attackers use these addresses to send messages to the impersonated user’s potential contacts with a sense of urgency while claiming the impersonated user can't be reached any other way, or they may request the victim’s phone number so that they can continue the scam over text message.
If a potential victim responds, the attacker requests the victim to purchase gift cards in varying denominations with their personal funds. The attacker will request that the victim send images of the gift cards so that the attacker may redeem them to steal the funds from the victim.
We recommend verifying suspicious or sensitive requests through a separate channel. For example, contact the user making the request directly via phone, in-person, or a known-good address to validate the request before making any purchases or following any instructions in the email.
[back to top]
Attackers abuse legitimate sharing platforms like OneDrive or Google Docs to send phishing messages and evade filters.
The messages will typically be sent from an external user. However, the description of the file may include a reference to an impersonated LSU user.
When the victim opens the shared file, it contains a link to a phishing site. These are called “Adversary in the Middle” phishing campaigns; the phishing site interfaces with Microsoft on your behalf and can even trigger an MFA verification request if you provide the site your account password. If the request is approved, an authenticated session is granted to the attacker.
Ensure the context of the message makes sense. If you receive an odd document you were not expecting from someone you don’t know, or if you get a message claiming to be a document from someone else, be very cautious with the message. If a shared file attempts to direct you to re-authenticate to view a shared document, use caution and always verify the sign on URL is accurate. Microsoft sign ins should occur at “login.microsoftonline.com”. Report suspicious documents and sharing requests to IT Security for further review.
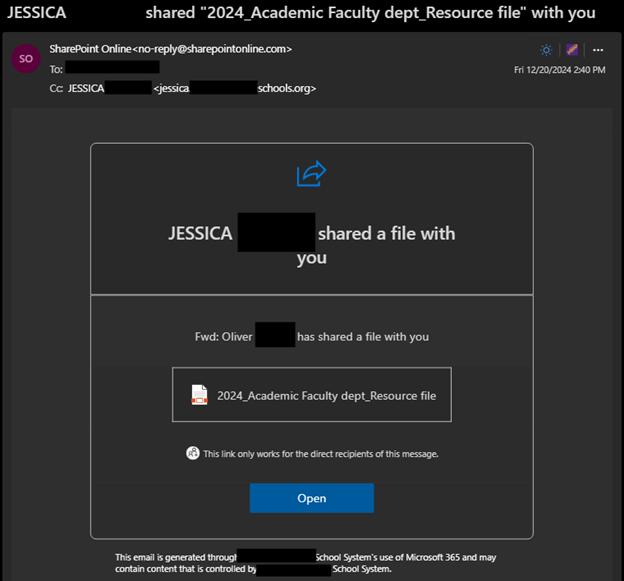
- Note that while this message was sent by “Jessica,” the description inside the message is an attempt to impersonate a different sender named “Oliver.”
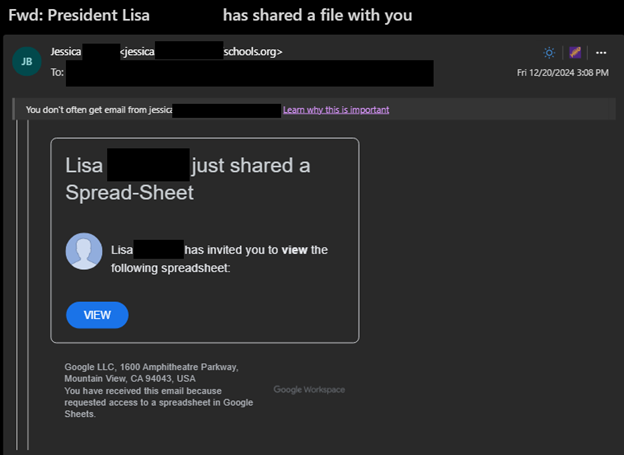
- In this example, the message is sent by “Jessica,” but a user named “Lisa” is being impersonated within the email.
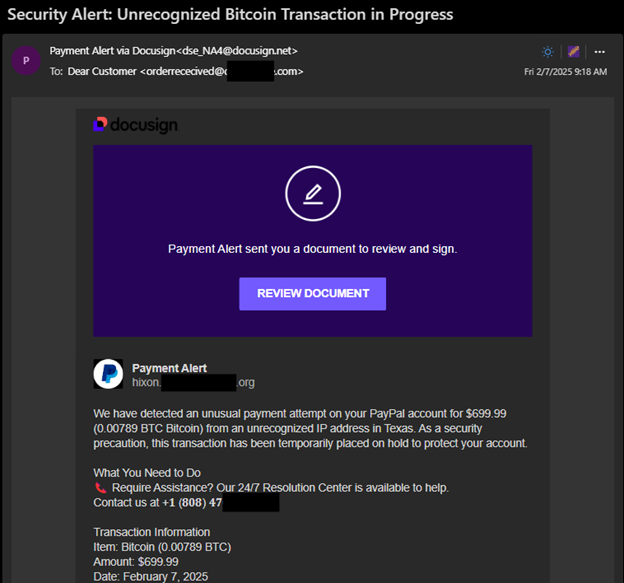
- While this message is not an attempt to steal user credentials but a financial scam, this is another example of a fraudulent document shared via abuse of a legitimate platform.
[back to top]
Scammers will create fake accounts, or will use compromised accounts that appear more credible, to send unsolicited job offers or other opportunities.
The scams will promise the victim a job, series of tasks, or will provide a check with excessive funds for a user to buy certain job materials. The payments from the scammer are not legitimate; when the scammer’s check does not clear, any money the victim uses or forwards on behalf of the scammer from the check funds may be lost.
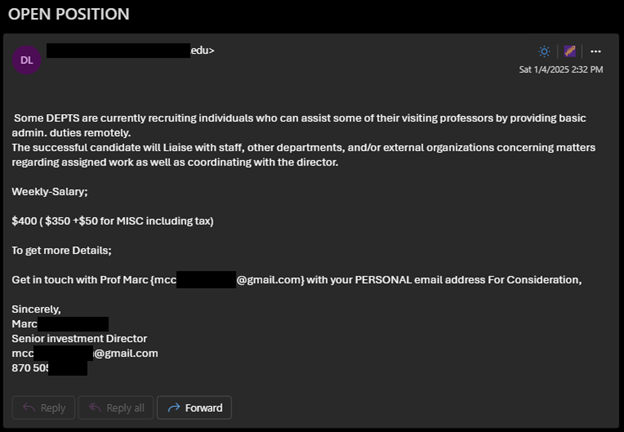
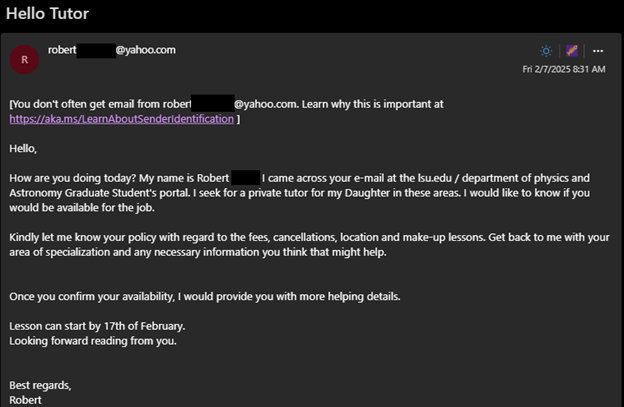
For more information, see this article from the FTC on "How to Spot, Avoid, and Report Fake Check Scams"
[back to top]
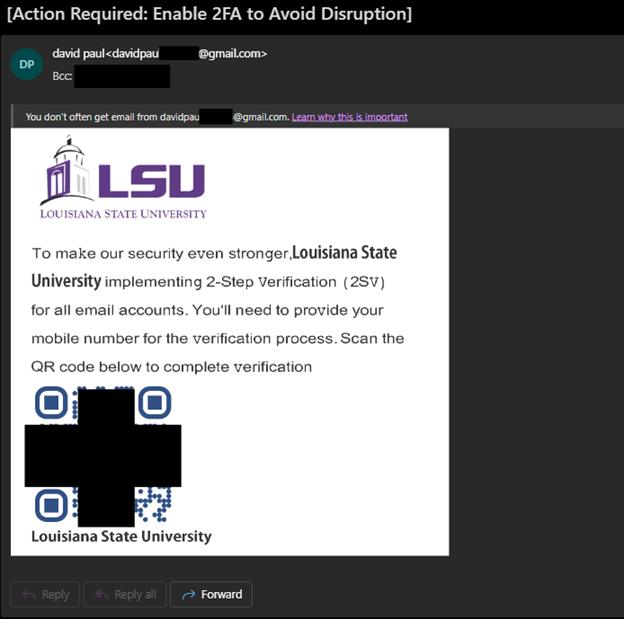
LSU will never send you an email with a QR Code for MFA enrollment! Instructions on MFA enrollment can be found here: Office 365: Multi-Factor Authentication (MFA) Enrollment
QR Codes are becoming popular vectors for phishing as they cannot be easily evaluated or blocked like traditional links.
Always be careful when visiting a site though a link in a QR code. If a QR code leads to a credentials prompt, exit the page and attempt to access the desired resource directly from a trusted link or URL.
[back to top]
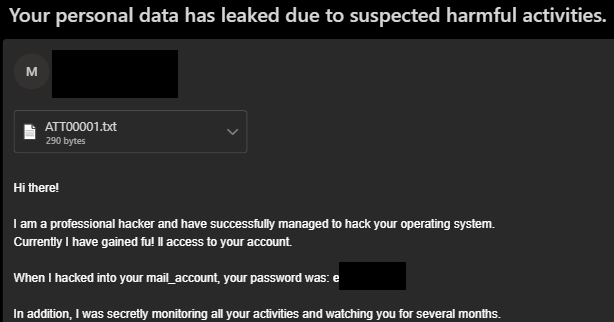
This is a common scam in which an attacker uses some combination of spoofing a victim’s email address, claiming to know their password, claiming that they have infected their computer, or providing knowledge of a user’s personal details like home addresses or phone numbers. The passwords, phone numbers, and addresses are sourced from leaked information from third party data breaches.
Often the attacker will make sensationalistic or offensive claims about the receiver to enhance the threat. These emails are fraudulent and can be safely ignored. Do not interact with the attacker and do not send any payments to the extortion address.
[back to top]
Report the message if you still have it. IT Security will review the message and can check your account for threats or suspicious access.
Change your password as soon as possible if it was provided in a form or on a phishing page. The new password must be unique and should not have been used anywhere else. If you use the same password for different services, you must change passwords for other services as well.
Monitor your accounts and banking statements for suspicious charges. Attackers will attempt to use compromised credentials on shopping sites to abuse saved payment details for fraudulent purchases.
Submit a request to LSU IT Security via a Security Consulting request from the IT Service Catalog or contact security@lsu.edu if you have any additional concerns regarding suspicious messages you have received or interacted with.
[back to top]